
By Jim L.
Have you ever wondered if the Cloud was really secure and how security measures and best practices were implemented? In this blog post we will review the major security concepts to assure confidentiality, integrity, and availability of systems and data in the Cloud. We will use AWS as the example environment, but the principles are applicable to other Cloud Service Providers (CSP) too.
First, let’s look at the concept of a Shared Security Model which defines what the CSP is responsible for and what you must do as the resource consumer. As you can see in the figure, AWS is responsible for securing and protecting the core infrastructure services and you are responsible for the identity and access management, content, security controls, and monitoring. AWS manages over 1,800 security controls so that you don’t have to, but you must still identify and define the use of the right security controls for your workload sensitivity.
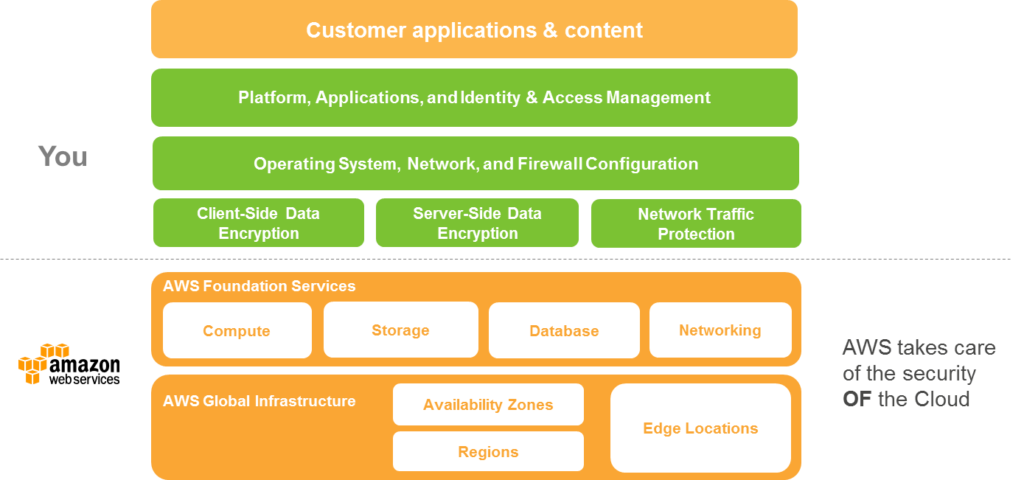
Example of a Shared Security Model
A Defense in Depth strategy is another important concept to implement security controls, countermeasures, and safeguards using administrative, logical/technical, and physical access controls to provide layered security. The adjacent figure portrays the major techniques to implement defense in depth for a Virtual Private Cloud (VPC). Starting at the bottom of the figure, the VPN gateway connection extends your on premise private network to the VPC and provides security and privacy on an encrypted connection. The open Internet should never be used as the transport to connect with your private network. The other ingress/egress point into the VPC is through the Internet Gateway. The Internet Gateway is a scalable, redundant, and highly available component that provides the public access point to the VPC. The VPC Router and route tables provide the next layer of security for your VPC; the route tables contain the set of rules that allow and deny network traffic within the VPC. Moving up the security stack, Access Control Lists and Subnets work together to control access and compartmentalize network boundaries. Subnets can be either internally Private or Public with Internet access. Finally, Security Groups act like a virtual firewall for one or more compute instances and they control inbound and outbound traffic to and from instances based on rules that you configure.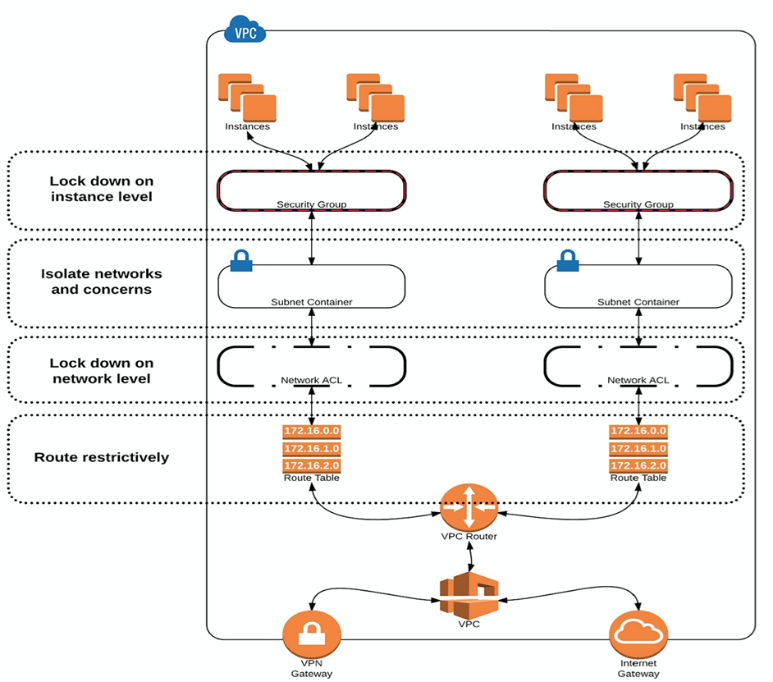
Example of Defense in Depth Strategy
Fundamentals like Shared Responsibility and Defense in Depth are only the tip of the security iceberg! The Cloud can be more secure than an on premise data center and much easier to manage. New tools and services are continually being deployed and many of them are free services. To learn more about security best practices check out these resources. AWS Security, Azure Security, Oracle Security, Google Security
